About
Risk Management
Risk Management Structure
Internal Regulations for Risk Management
We consider risk management to be a key priority to ensure the continuity and stable development of our businesses and endeavor to take an active approach to risk management across our operations. We have established the Recruit Group Risk Management Regulations, which provide a comprehensive risk management structure and reporting system for the entire group, and the Recruit Group Escalation Bylaws, which aim to achieve prompt reporting and information sharing related to major issues within the Company.
Risk Management Committee
The Holding Company established the Risk Management Committee, which serves as an advisory body to the Board of Directors, with Senior Vice Presidents as members. The Committee monitors the status of each of the SBU risk management functions, and engages in comprehensive discussions concerning the risks affecting the Company based on a group-wide risk map addressing the risk items of the Company including each SBU. The Risk Management Committee then selects the high-priority risks of the Company and implements appropriate countermeasures including monitoring policies.
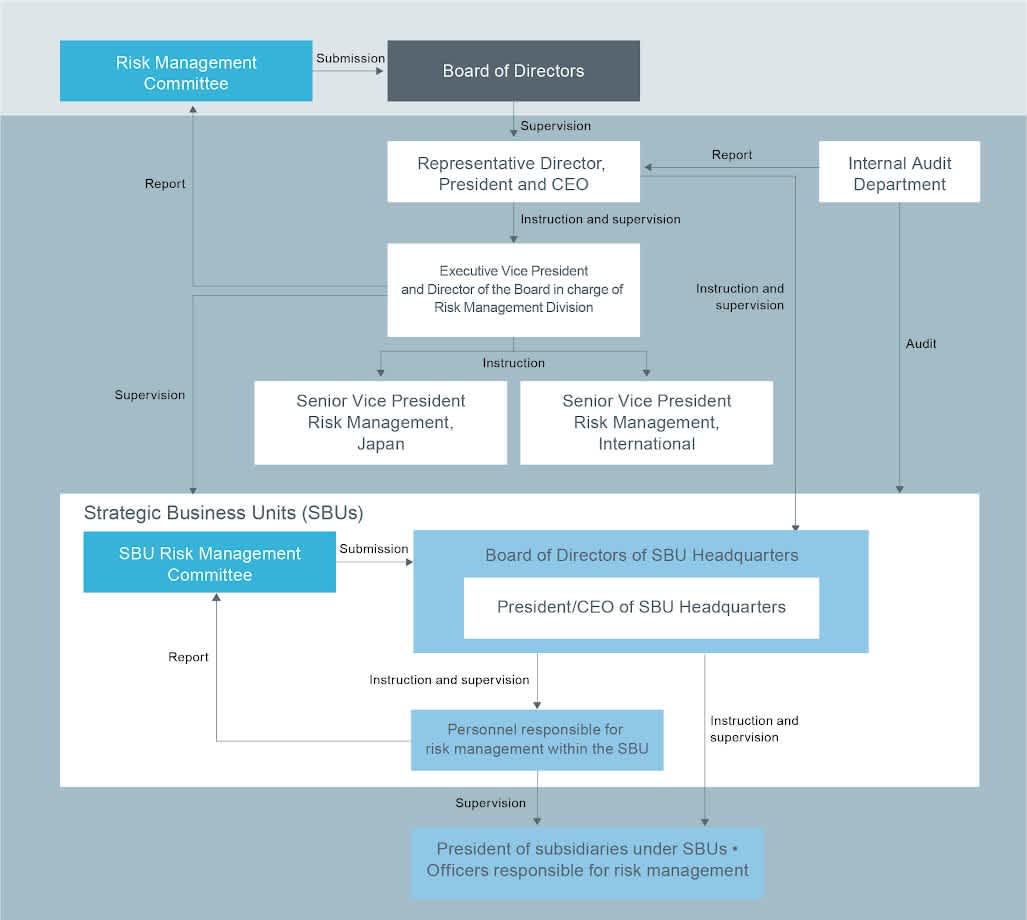
Risk Management Structure in the Holding Company and Each SBU
We have established the position of Director in charge of the Risk Management Division, and this Director also serves as our Executive Vice President. Because we believe that the viewpoints and perspectives appropriate for responding to such risks differ between Japan and overseas markets, we have assigned separate Senior Vice Presidents in charge of Japan (Risk Management Japan) and overseas (Risk Management International) matters to serve under the Risk Management Division of Recruit Holdings with the aim of responding to the high-priority risks applicable to each relevant region in a manner that is appropriate to the characteristics of such region.
The department in charge of risk management shares information and collaborates with our Internal Audit Department in a timely manner so that our Internal Audit Department can efficiently conduct operational audits of the status of responses to high-priority risks of the Company.
Risk management structure of each SBU is as follows.
Subsidiaries of each SBU are required to carry out risk management functions by identifying relevant risks, assessing materiality of such risks, and implementing countermeasures in response to such risks. The SBU Headquarters of each SBU appoints personnel responsible for risk management within the SBU with the task of overseeing the risk management function of the SBU and monitoring the risk management status related to the business of the SBU including its subsidiaries.
The SBU Risk Management Committee convenes on a semi-annual basis in order to assess and discuss the risks concerning the businesses operated under the SBU, determine high-priority risks relevant to the SBU and implement countermeasures, and monitor the risk management status of such risks. The Executive Vice President and Director in charge of the Risk Management Division of Recruit Holdings also participates in the SBU Risk Management Committee meetings to oversee the status of risk management functions in each SBU.
The Risk Management Division of the Holding Company, which oversees the secretariat of the Risk Management Committee, regularly reports on risk management activities to our Board of Directors, and has established a structure and reporting system that enables the Board of Directors to properly monitor the status of risks affecting the Company and the countermeasures in response to such risks.
Our Risk Management Structure
High-Priority Risks and Key Countermeasures
Among the risks that may affect the Company's financial condition, results of operations and cash flows, the high-priority risks that the Directors and Senior Vice Presidents perceive to be of particular importance and require countermeasures are as follows.
High-priority Risks
Risks associated with Data Security and Data Privacy
Risk Awareness
The Company acquires, manages, and utilizes personal information, including the information of a large number of individual users, in each of our SBUs. We believe it is our obligation not only to comply with the laws of each area and country, but also to respect and protect the privacy of individual users in conformity with the expectations of society.
In the unlikely event of an incident involving personal information, this may not only cause great inconvenience to individual users, but we may suffer from a loss in the value and reputation of our brand and confidence in our services from our individual users. We are also aware that we may be subject to business suspension orders, fines and other sanctions by the authorities, as well as lawsuits filed by individual users or business clients, which could seriously harm the Company's operating results.
For this reason, the Risk Management Committee of Recruit Holdings and the Risk Management Committee of each SBU recognize that data security and data privacy are high-priority risks and continue to implement appropriate measures.
Key Countermeasures
Depending on the importance of the data or information in our possession, as well as the characteristics of the data or information to be protected, we have established structures and reporting systems, and measures necessary for each country and area's laws and regulations. For example, we monitor for unauthorized access, detect and block computer viruses, preserve communications and access records that may be used for investigations, and conduct periodic vulnerability tests.
Countermeasures relevant outside of Japan (overseas)
In order to meet industry requirements with regard to data privacy, we have established standards for responding to the laws and regulations in each jurisdiction, such as the GDPR in Europe, CCPA in the State of California, United States, and others. With regard to data security, we have established reference standards such as NIST, ISOs, and CIS20, according to the business and risk characteristics of each SBU.Countermeasures relevant to Japan
With regard to data privacy, we have established a “Personal Data Policy” and established a privacy center. With regard to data security, we have established dedicated security departments, such as Recruit-CSIRT, to detect damage at an early stage, implement measures to minimize such damage and prevent data breaches.
The Company is proceeding with the implementation of the above measures upon consideration of the necessity of such measures as well as the order of priority of implementing various measures with respect to each subsidiary within the Company.
For more details, please refer to "The Company may be subject to liability and regulatory action or suffer reputational damage if the Company is unable to maintain the security and the privacy of its data or maintain effective policies and procedures for the storage, management, usage and protection of personal, confidential or sensitive information. " in the "Risks That May Affect the Company's Financial Condition, Results of Operations and Cash Flows" in the Annual Report, translated from Yukashouken Houkokusho for FY2022 and "Data Security and Data Privacy
" in the ESG Data Book.